FBI obtained detailed database exposing 60,000 users of the cybercrime bazaar Genesis Market

The FBI obtained copies of back-end servers related to Genesis Market, providing law enforcement with detailed information about the cybercriminals who used the marketplace to trade in stolen credentials and access to compromised computers, senior FBI and Department of Justice officials said Wednesday.
The systems obtained by the FBI “included information about approximately 59,000 individual user accounts,” an official told reporters. The data includes usernames, passwords, email accounts, secure messenger accounts and user history. “Those records helped law enforcement uncover the true identities of many of the users,” the official said.
The full scope of what more than a dozen international law enforcement agencies call “Operation Cookie Monster” — a massive investigation that resulted in the seizure of the Genesis Market — is still coming into focus.
So far, officials have said the operation involved more than 400 law enforcement actions across 15 different countries and included 119 arrests, 208 searches and interviews “across the globe.” There have been “domestic activities” in the U.S. involving the FBI, one official said, including arrests, but the official declined to share details on the arrests.
Operation Cookie Monster is “the largest operation to investigate those offering and purchasing stolen credentials that we have ever conducted,” one of the officials said. The Genesis Market disruption and last month’s arrest of the alleged owner and operator of BreachForums, which led to the demise of that site, represent significant action against the two largest marketplaces selling stolen credentials “which have been taken offline, both in 30 days time,” an official said.
At least two of the domains and login pages for Genesis Market remain active, including both the site on the open internet and the dark web version. Someone claiming to be affiliated with Genesis posted to another forum Wednesday that the site was working at its old address via the Tor browser. “Now there will be a lot of fake shop domains, do not enter your username and passwords into unknown URLs,” the user by the name of “terabyte” wrote, according to a screenshot shared with CyberScoop by Austin Martin, an independent researcher based in Pittsburgh. “New web domains will be announced soon.”
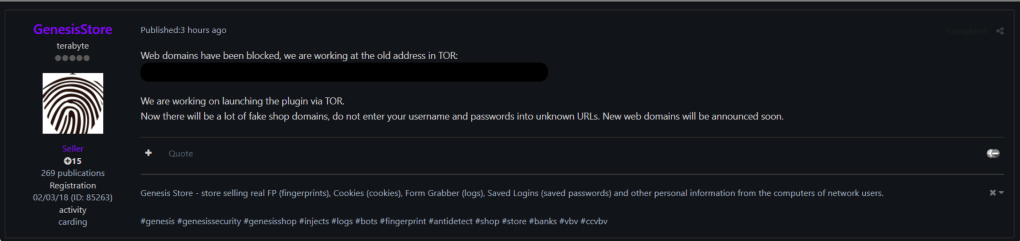
The senior FBI and Department of Justice officials on Wednesday declined to discuss specifics related to the enduring Genesis Market domains. “We have an ongoing investigation, and the actions that we’ve taken have allowed us to disrupt Genesis in ways that may not necessarily be seen or apparent to others,” an official said.
Operation Cookie Monster is just the latest aggressive U.S. government action against the cybercrime ecosystem. Conor Fitzpatrick, the 20-year-old accused of owning and operating BreachForum, was arrested at his family’s home in New York last month. In January, the U.S. Department of Justice seized servers associated with the Hive ransomware variant after spending months inside the group’s networks, ultimately providing more than 300 decryption keys to victims the group targeted, the agency said. Other disruptions include the international operation to disrupt the Hydra market, RaidForums, cyrptocurency exchangers and mixers, and individual ransomware operators.
The U.S. government is focused on “proactive, disruptive activities” against the cybercrime ecosystem that enables everything from business email compromise to ransomware to illicit activity by nation states, the official said
“We have got to increase the risks for these individuals to engage in this activity,” one of the officials said. “I think as you’ve seen over the last year, and particularly over the last few months, actions that we’re taking are increasing the costs for what they are engaging in.”
Another official speaking Wednesday noted that arrests and other law enforcement actions undermine trust as much as the actual infrastructure involved. “If you’re a user of this site it may make you think twice about whether this is a good place to be doing business, whether you might be identified as result of law enforcement activity against the site,” the official said. “There may well be difficulties for the reconstituting of the site in terms of the trust of its criminal user base.”





