FBI warns industry that hackers could probe vulnerable connections in building systems

A port for communicating with control systems in buildings leaves unpatched devices on those networks exposed to hackers, the FBI warned the private sector this week, calling attention to a longstanding issue in an often-overlooked segment of critical infrastructure.
Major universities, state governments, and communications companies are among the organizations at risk of having their building-system data exposed, the bureau said in an industry advisory obtained by CyberScoop. The port in question – port 1911 – is serving up building-network information on the internet that could be of use to hackers.
“This default port discloses system information without authenticating, allowing cyber attackers to identify devices and systems that are not patched against known exploits,” the FBI alert says. “Successful exploitation could lead to data leakage and possible privilege escalation.”
An FBI spokesperson told CyberScoop that the bureau “routinely advises private industry of various cyberthreat indicators observed during the course of our investigations.” That data is provided “to help systems administrators guard against the actions of persistent cybercriminals,” the spokesperson added.
While the advisory raised concerns around the ubiquity of internet-connected buildings, it did not mention any cases of hackers exploiting that access. Industry experts told CyberScoop they had not observed any recent compromises.
The concern is that attackers can collect data on a building network to eventually gain further access to the system. That said, the potential impact of a vulnerability in a heating and cooling system is not very high, according to Reid Wightman, an analyst at industrial cybersecurity company Dragos. Were hackers able to manipulate temperature settings in a building, that access would likely be cut off quickly, he said.
The default port setting mentioned by the FBI is not a new issue, rather a nagging one: researchers have raised concerns about the “Fox” protocol used to connect to the port since at least 2012. But thousands of devices appear to be using the port’s insecure connection today.
As of November, more than 700 industrial control systems (ICS) on U.S.-based networks accepted connections through the port from random IP addresses, the FBI said. However, Billy Rios, a security researcher who has tracked the Fox protocol for years, told CyberScoop the number of exposed systems is likely much higher than 700.
Rios, founder of embedded-device security company WhiteScope, maintains a database of internet-connected buildings. Over 50,000 of the buildings in that database use the Niagara Framework software, which the Fox protocol supports.
A query of Shodan, the search engine for Internet-connected devices, turned up nearly 20,000 connections in the U.S. alone for the Fox protocol via the default port the FBI referenced.
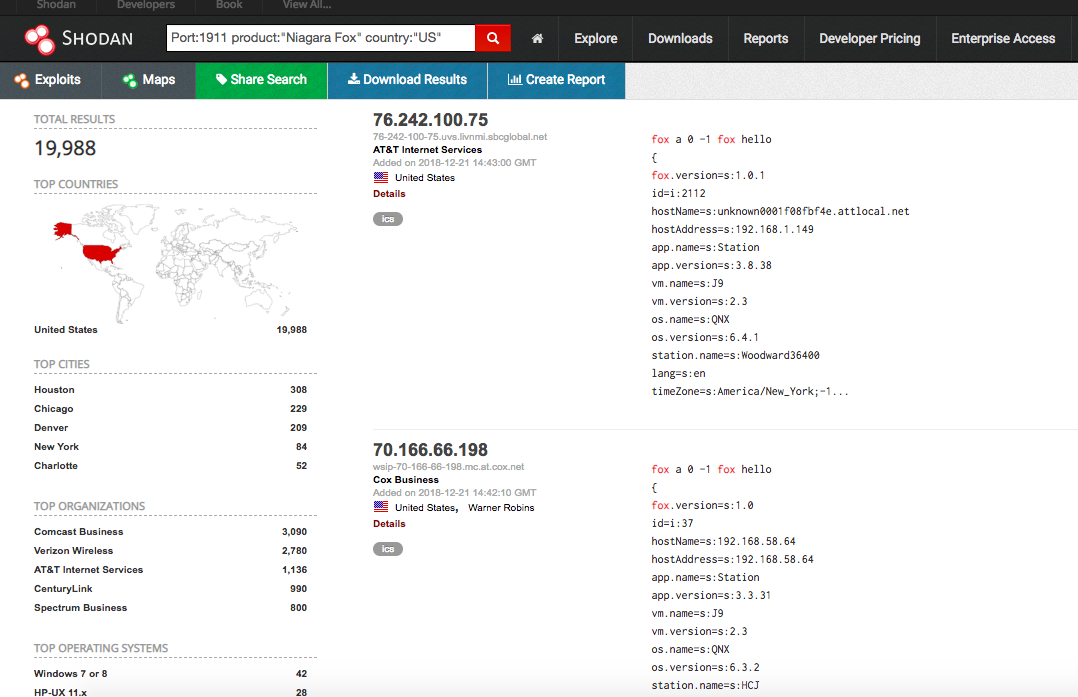
A screenshot from Shodan showing the amount of port 1911 and Niagra Fox. (Shodan.io)
‘A different threat model in mind’
The Fox protocol was developed by Richmond, Virginia-based Tridium Inc., which makes the Niagara Framework software that companies and government organizations around the world use to manage control systems in buildings. Tridium has been grappling with security challenges associated with the Niagara Framework for years.
In 2012, Rios and another researcher, Terry McCorkle, revealed a vulnerability in the Fox protocol that could allow hackers to download user names and passwords from the Niagara Framework. That was the year the software passed more than 300,000 installations, making it one of the most widely used internet-of-things platforms, according to the company website.
Tridium issued a patch for the Fox protocol vulnerability uncovered by Rios and McCorkle, and has continued to update its products.
But according to Rios, the authentication issue raised this week by the FBI is a default feature rather than a vulnerability, so there is no patch. When connected to the port, the protocol beams out on things like the host’s operating system and versions of the Niagara framework installed – information that would be useful for an attacker.
Wightman, the Dragos analyst, said the Fox protocol was designed with “a different threat model in mind,” adding: “They probably weren’t imagining that many of these systems would be connected to the internet someday.”
Building operators can protect the Niagara Framework by shielding it from the internet, deep into their operations network, or with a firewall or virtual private network, Wightman said.
Alternatively, Rios said, building system operators can turn off the protocol and use another one, to avoid broadcasting so much information online.
In a statement, Tridium said the FBI advisory referred to “old vulnerabilities that were responded to and resolved with security updates and patches when they were first identified.” The company advised customers to keep all of their software up to date, and pointed to security guide on its website.
“Cybersecurity is a priority we share with our customers,” Tridium added. “We will continue to assess and test the effectiveness of our products and solutions.”
Building-systems security lags
The building-automation sector has lagged behind others in network defense, experts said. While security practitioners have paid greater attention to the ICS field as a whole in recent years, the subsector of building automation has been neglected, said Eddie Habibi, founder of energy-security company PAS Global.
The fact that buildings aren’t considered the most critical of ICS-related infrastructure has bred “a sense of complacency” in the industry about tackling building-protocol vulnerabilities, Habibi told CyberScoop.
“The maintenance personnel responsible for these systems probably don’t keep up with the cybersecurity threats that are out there,” he said.
Another issue is that there is not much of a market for securing building control systems compared with other ICS sectors, Dragos founder Robert M. Lee said.
“The lack of resources available limits the focus on security and the majority of customers don’t perceive the risk high enough to pay for more secure products or address the risk through other means,” Lee added.






