Feds upping their email security game in wake of DHS order

The number of federal agencies employing a security protocol that stops email spoofing has more than doubled since the Department of Homeland Security instituted a binding government-wide policy last month.
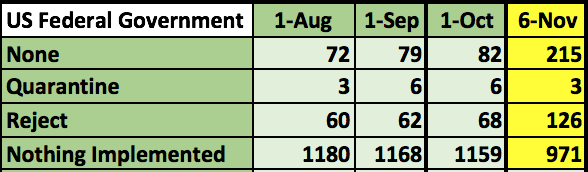
The number of .gov domains employing Domain-based Message Authentication, Reporting and Conformance (DMARC) has risen from 156 on Oct. 1 to 344 on Nov. 6, according to figures compiled this week by the nonprofit Global Cyber Alliance.
Nearly a thousand federal domains still don’t have it deployed at all, despite the Binding Operational Directive DHS issued Oct. 16.
DMARC is the industry standard measure to prevent email spoofing — when hackers make their messages appear as if they come from trusted correspondents. It’s thereby a powerful weapon against phishing — when hackers try to steal passwords or implant malware by getting victims to click links or open malicious attachments in spoofed emails.
But DMARC, once deployed, has to be switched on, explained GCA’s Director of Operations Shehzad Mirza.
“DMARC needs to be implemented,” he told CyberScoop, explaining that protocol can be set to one of three levels.
If both sender and receiver have the policy at “quarantine,” email attempting to spoof the sender’s address will be delivered to recipient’s spam folder. If DMARC is switched to its highest setting — “reject” — the spoofed mail will not be delivered at all.
But if DMARC is set to a policy of “none” — as with nearly two-thirds of the federal agencies that have it deployed — spoofed mail will be delivered as normal. The domain owner will be sent reports of any spoofing of their domain.
DMARC is a way of enforcing something called Sender Policy Framework (SPF) — a public record of “who is authorized to send email on behalf of that domain,” explained Mirza.
According to SPF records, Mirza said, 96 of the .gov domains with DMARC are not used by the government for sending email. The SPF policy is set in such a way that “no one is authorized to send email on behalf of that domain.” This is a form of defensive registration quite common for large companies, to ensure — as a fictive example — that no one can send email purporting to come from IRSCustomerService.gov. There are more than 100 other domains with a similar SPF policy, but where DMARC has either not been deployed or not been switched on.
“It’s possible that is temporary, while they are researching,” said Mirza, noting “Those agencies might be either confirming that email is used for those domains or be in the process of amending their SPF records after reviewing DMARC reports.”
Large organizations often have multiple contractors or email servers sending from their domain and switching DMARC on without ensuring all those are authorized by the SPF policy can result in service interruptions, eg for marketing emails from a third party contractor.
DMARC deployment by federal agencies before and since DHS issued a Binding Operational Directive Oct. 16 (source: Global Cyber Alliance)
Moreover Mirza said, nine of the agency domains that have implemented DMARC have done so without enabling reporting. Four of those are using DMARC level none without reporting.
“What’s the point?” he asked. “The reason for having none is so you can look at the reports and figure out what changes you might need to make.”
“Those reports contain good cyber intelligence,” about attempts to spoof and phish federal domains, he said.
DMARC grew out of a 2007 effort by PayPal and Yahoo to stop rampant email phishing of PayPal users. They succeeded in leveraging two existing email security standards — Sender Policy Framework and Domain Keys Identified Mail (DKIM) — to ensure that spoofed email would not be delivered.
A working group of email experts from many tech firms, financial institutions and e-commerce companies called the Messaging Operational Overlay Coalition Of the Willing, (MOOCOW) worked for five years to turn DMARC into a generalizable standard, according to a brief history published by email security outfit Agari.
Three years later, in 2015, it was published by the Internet Engineering Task Force. Now, the vast majority of consumer email providers enable it, meaning if a sender has it activated, no spoofed email from that address will be delivered.






