Notorious Genesis Market cybercrime forum seized in international law enforcement operation

More than a dozen international law enforcement agencies took down a notorious cybercrime marketplace on Tuesday, shuttering an illicit website called the Genesis Market known for selling compromised credentials and biometric data for digital fraudsters to carry out attacks or commit identity theft.
The FBI-led effort known as “Operation Cookie Monster” also included “a large number of arrests,” according to The Record, which first reported the news. Genesis Market had been linked to “millions of financially motivated cyber incidents globally,” according to The Record.
The operation on Tuesday involved 17 countries and resulted in 119 arrests, 208 property searches and 97 “knock and talk measures,” according to a statement posted by Europol on Wednesday. In the U.S., the operation spanned 45 FBI field offices, led by the Milwaukee Field Office, the U.S. Department of Justice said Wednesday.
The seizure is just the latest in a wave of aggressive U.S. government cybercrime operations targeting the infrastructure supporting the criminal digital underworld. Last month, the FBI arrested the owner and administrator of BreachForums, and the remaining administrator decided to shutter the site down after documents revealed the FBI had access to internal site data. In January, the FBI and the Department of Justice announced it had hacked into and spent months inside the Hive ransomware networks before seizing the site.
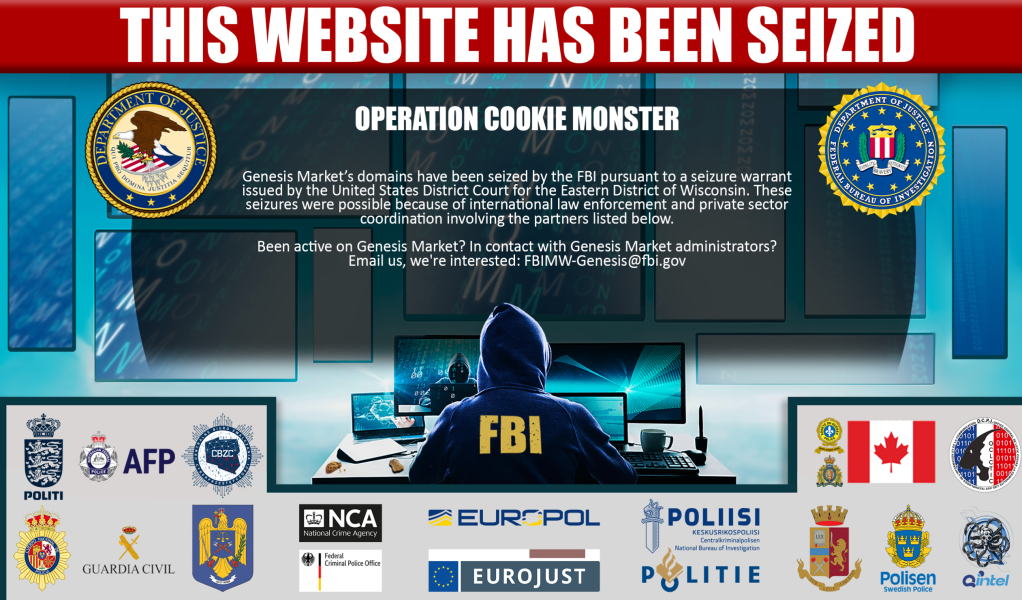
A takedown notice appeared on the Genesis front page on Tuesday showing a hooded FBI agent working at a computer. “This website has been seized,” the notice read, noting that a seizure warrant was issued by a federal court in the Eastern District of Wisconsin. The notice included a note to the site’s users: “Been active on Genesis Market? In contact with Genesis Market administrators? Email us, we’re interested,” the note read, followed by an FBI-related email address.
The FBI did not immediately responded to a request for comment.
Troy Hunt, an Australian security researcher and the man behind the Have I Been Pwnd databreach notification service, wrote Wednesday that the FBI provided his site with “millions of impacted email addresses and passwords … so that victims of the incident can discover if they’ve been exposed” through an email notification system on his site.
Will Thomas, a CTI researcher at Equinix, noted on Twitter that “if your email appears in this you might have been infected with an Infostealer at some point, probably a lot of other accounts that need creds rotating.”
Ruben Van Well, a member of the Rotterdam police cybercrime team in the Netherlands, said in a statement that given the nature of the malware associated with Genesis, “changing passwords is not enough,” and that a more thorough check of your system is required if there are indications your email was involved.
Researchers with the Trellix Advanced Research Center said Wednesday they were approached by law enforcement asking for assistance with the analysis and detection of malware linked to Genesis Market. “The primary goal was to render the market’s scripts and binaries useless,” the researchers wrote in a paper that shared background on the market and technical details and indicators associated with the malware.
Alexander Leslie, an associate threat intelligence analyst with Recorded Future, wrote in a Twitter thread Tuesday that Genesis was “one of the world’s largest ‘log’ shops,” and explained that the type of data and tools sold on the site could be used to assume the identity of an actual person’s browser, making “multi-factor authentication (MFA) bypass incredibly effective.”
In an February 2020 analysis, Israeli security researcher Alon Gal reported that, at the time, the site was offering 230,000 “infected computers you can buy the logs from.” The analysis demonstrated how Gal could have purchased multiple login credentials for multiple sites obtained from the browser of one infected computer. User experience on the site was “professional, much like what one would expect to see on any ecommerce site,” researchers with cybersecurity firm F5 Labs wrote in November 2020. A user could search for “specific brands, credentials from a particular website, or specific data types like a credit card,” the researchers wrote.
In June 2021, hackers who claimed to be involved in the Electronic Arts hack told Vice’s Joseph Cox that they purchased a $10 browser cookie that let them log in to an EA Slack account, a key step in the process that enabled the theft of at least 780 gigabytes of data.
By the time of the April 4 law enforcement operation, the market had more than 1.5 million bot listings representing more than 2 million identities, Europol said.
Updated, April 5, 2023: This story has been updated to include information from Europol, the Netherlands Police, Have I Been Pwnd, the Trellix Advanced Research Center and the U.S. Department of Justice.






