FBI to private industry: Attribution won’t deter North Korean hacking

The FBI has told American companies that North Korean government hackers will continue to target financial institutions worldwide despite the U.S. government’s public attribution of such activity to Pyongyang.
The targeting “will continue unabated, regardless of the U.S. government public attribution of North Korea,” the FBI’s cyber division said in an industry advisory dated Oct. 25 and obtained by CyberScoop. “North Korean cyber activities remain a concern based on its historical patterns of behavior,” the notice says.
In conceding that attribution will not change North Korea’s calculus in cyberspace, the FBI is reiterating what is widely recognized in the cybersecurity industry: that Kim Jong Un’s regime is too brazen to care about being called out for its hacking.
In September, the DOJ announced charges against North Korean spy Park Jin Hyok for his alleged role in the destructive 2014 cyberattack against Sony Pictures Entertainment and the 2017 WannaCry ransomware attack. It was the first time the U.S. government had charged a North Korean for hacking. Analysts told CyberScoop that the broad set of North Korean hackers that includes Park would be undeterred and continue to evolve and clean up its operational security.
In the Oct. 25 alert, the FBI said it “does not have reporting to indicate North Korea will likely retaliate based on the unsealing of the complaint.”
The advisory is labeled “Traffic Light Protocol (TLP) Green,” meaning private-sector recipients can share it with partner organizations but not publicly. TLP classifications measure the sensitivity of threat information the government disseminates to the private sector.
“In furtherance of public-private partnerships, the FBI routinely advises private industry of various cyberthreat indicators observed during the course of our investigations,” an FBI spokesperson told CyberScoop. “This data is provided in order to help systems administrators guard against the actions of persistent cyber criminals.”
DOJ officials have argued that, regardless of whether a hacker sees the inside of a U.S. courtroom, bringing charges sends an important message that the hacking will not be tolerated. The efficacy of U.S. deterrence tools – whether sanctions, public shaming, offensive cyber operations, or other measures – vary depending on the foreign government targeted.
In response to North Korea’s testing of nuclear weapons and missiles, the U.S. government has repeatedly imposed economic sanctions to squeeze the Kim Jong Un regime’s financing. Under that pressure, the Pyongyang has used hacking operations to raise significant money, according to researchers.
In the weeks that followed the DOJ charges against Park, cybersecurity company FireEye released evidence documenting a distinct group of North Korean hackers that has helped finance the Kim Jong Un regime. “This is an active … threat against financial institutions all around the world,” FireEye’s Sandra Joyce said in announcing the research.
The Oct. 25 FBI alert lists some of the tactics and techniques North Korean hackers have used to target the financial and energy sectors in recent years. The North Koreans have used spear-phishing on both sectors, while employing custom malware to hit financial institutions and a master boot record wiper malware against the energy sector, the alert says.
The FBI advisory also attributes “the leak of a foreign power plant blueprints” to North Koreans, which is likely a reference to a December 2014 breach of a South Korean power company’s IT system. The hackers stole the blueprints of Korea Hydro and Nuclear Power Co. nuclear reactors along with the company’s estimates of radiation exposure to local residents.
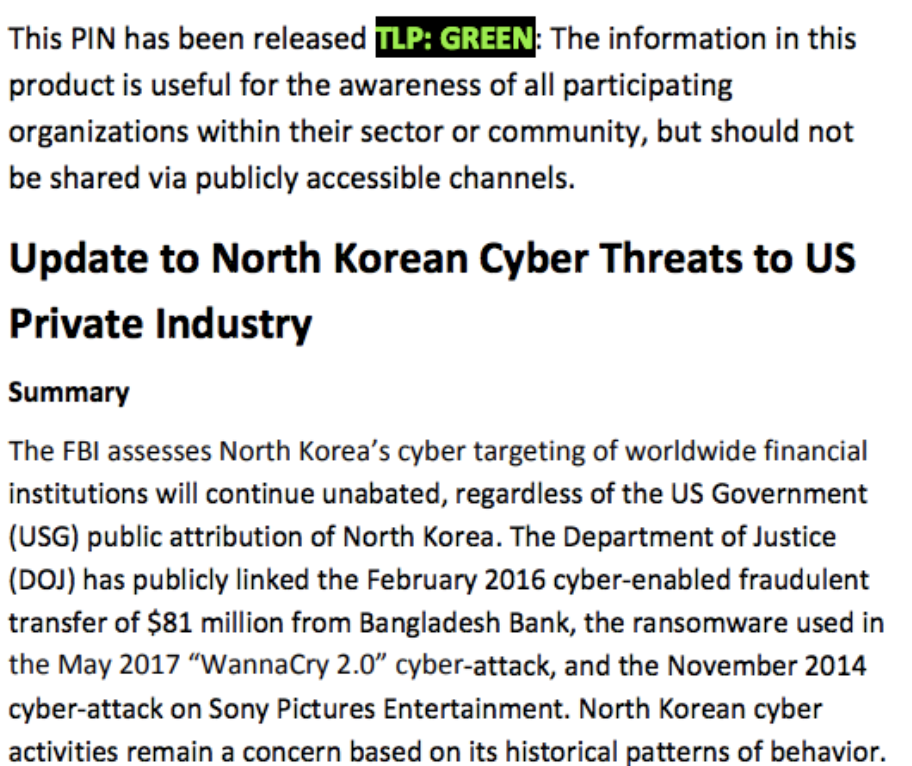
A screenshot of the FBI alert is below.