‘Nation-state’ hackers increase sabotage attempts aimed at Western energy companies

A well-resourced hacking group known as Dragonfly is actively and successfully targeting U.S. and European energy companies in a campaign stretching back to 2015, and researchers say it has gained unprecedented access to operational systems of Western power companies.
Researchers for security firm Symantec who discovered the campaign warn that “the group now potentially has the ability to sabotage or gain control of these systems should it decide to do so.”
Dragonfly — also known as Energetic Bear, Koala and Iron Liberty — has been attributed to Russia and is categorized it as an advanced persistent threat (APT). Researchers say it has been active since 2010 and operated in secrecy until spotted in 2014 by Symantec, CrowdStrike and FireEye.
The group’s goal appears to be surveillance, as well as access to the oil, gas and energy industry in the U.S., Turkey and Switzerland. Its hacking activity has spiked in 2017, researchers said.
Robert Lee, CEO of cybersecurity company Dragos, told CyberScoop that people shouldn’t be alarmed, though. It’s still a significant challenge, he said, to escalate from gaining access to a energy’s company’s IT infrastructure to actually cutting off power. Dragos works to secure the types of industrial control systems that are crucial to power plants and other facilities.
“The companies we’ve spoken with are taking this very seriously and that’s a good sign that the public can feel safe and proud of our resilient infrastructure,” Lee said.
Dragonfly uses malicious email phishing campaigns and watering hole attacks to steal credentials and gain access to sensitive systems.
“When we looked at Dragonfly in 2014, they were a classic nation-state-level group that used a lot of their own custom malware,” Symantec researcher Eric Chien said. “It seems like they’ve sort of retooled now. They’re relying heavily on off-the-shelf toolkits and backdoors modified for their own use. Just the notion of doing so makes it very difficult to attribute their activity.”
For most of Symantec’s investigation, researchers had not actually made the connection the Dragonfly’s earlier activity. They also did not think the two attack waves were linked and from the same group. Only later did Symantec’s research reveal that Dragonfly is reusing specific custom malware (Trojan.Heriplor) linked previously to the group, thus establishing the strongest link between the two periods. There are other malware commonalities but none were totally exclusive to Dragonfly.
“We’re not in a position to confirm this activity is tied to the Dragonfly threat actors, but Symantec has historically done good work on that threat,” Lee added. “The public connection is weak, but Symantec likely has additional datasets.”
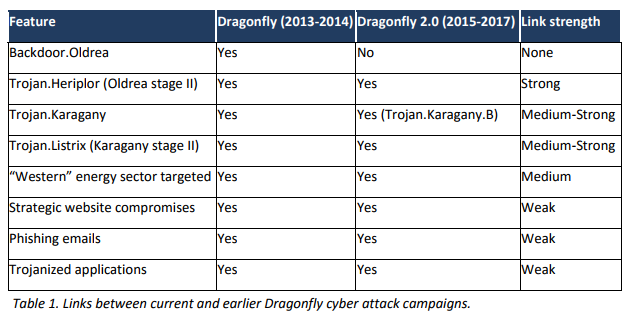
Symantec’s links between Dragonfly campaigns
The next step could be sabotage.
“The original Dragonfly campaigns now appear to have been a more exploratory phase where the attackers were simply trying to gain access to the networks of targeted organizations,” Symantec’s research explained. “The Dragonfly 2.0 campaigns show how the attackers may be entering into a new phase, with recent campaigns potentially providing them with access to operational systems, access that could be used for more disruptive purposes in future.”
It would be unprecedented in the U.S., of course, but Ukraine — a country now notoriously known as the testing ground for cyberwar — has experienced cyberattacks against its energy sector and subsequent blackouts in 2015 and 2016. Ukrainian security services blame Russia.
“We have not seen this scale of attack, the aggressiveness and penetration, in the U.S. before,” Chien said.
Chris Bing contributed to this report.






