Cybercrooks tried to steal these identities in just nine minutes

Cybercriminals took just nine minutes to start trying to rob a set of 100 synthetic “victims” whose fake personal information was posted online in an experiment by Federal Trade Commission officials over the past few weeks.
The speed of exploitation efforts might be linked to the fact that this posting — one of two dumps of the same fake data officials made in an effort to better understand how the exploitation of online accounts happens in real life — was noticed by a Twitter bot geared toward tracking any new data possibly useful for identity theft.
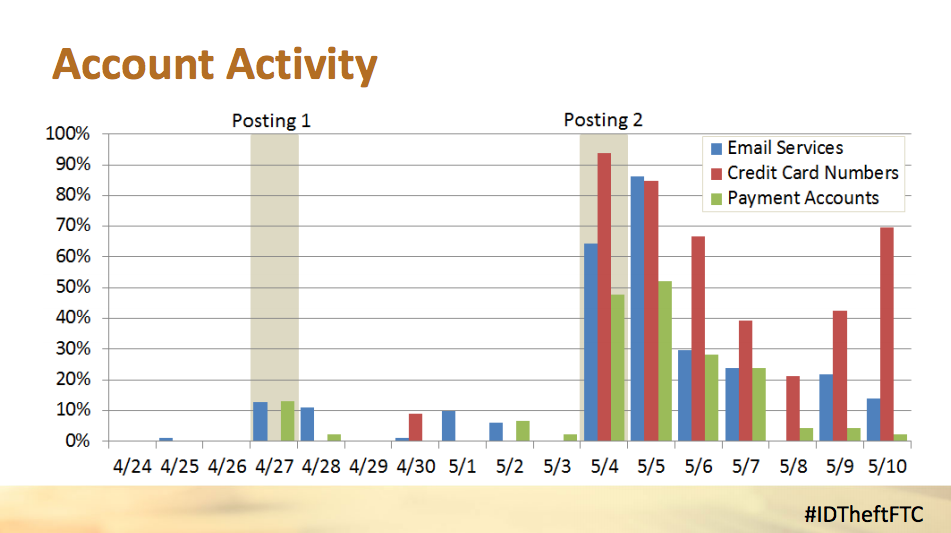
At the agency’s workshop on identity theft last week, officials unveiled their bold experiment: In late April and early May they posted online a database of 100 fake but believable identities and watched what cybercriminals tried to do with them.
“This wasn’t a typical data dump of sensitive information,” announced Dan Salsburg of the FTC’s Office of Technology Research and Investigation. “In fact, I have a surprise for the ID thieves out there that attempted to use this data. The FTC created and posted this database and we tracked how you used the data.”
“That’s right, ID thieves, you were part of an FTC study,” Salsburg said to a smattering of laughter.
Importantly, he noted, the database was dumped not to some obscure .onion address on the dark web, but to “a publicly available paste site” on the regular internet.
The posted database consisted of 100 “realistic” consumer identities, Salsburg explained: names; real addresses matching the area codes of phone numbers; email addresses with one of four major free cloud providers and employing common addressing conventions (like firstname.lastname); a payment mechanism — either a credit card number or an online payment account like PayPal or a bitcoin wallet; and a password.
“We did not identify what the passwords were for — for email accounts, payment account or something else,” Salsburg said.
“Most of the passwords were incorrect,” he said — meaning they didn’t actually grant access to any of the the accounts. For a small number of the accounts, the password worked for the email account, he said, but “we protected it with two-factor authentication.”
The two dumps happened April 27 and May 4.
Source: FTC
The same data was released, but in a different format, and at a different time of day, said Salsburg.
The second dump was noticed and tweeted by the Twitter bot, noted the FTC’s Christina Yeung.





