Conti ransomware group announces support of Russia, threatens retaliatory attacks

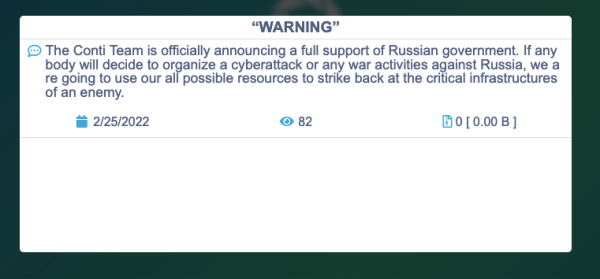
An infamous ransomware group with potential ties to Russian intelligence and known for attacking health care providers and hundreds of other targets posted a warning Friday saying it was “officially announcing a full support of Russian government.”
The gang said that it would use “all possible resources to strike back at the critical infrastructures” of any entity that organizes a cyberattack “or any war activities against Russia.” The message appeared Friday on the dark-web site used by ransomware group Conti to post threats and its victims’ data. Security researchers believe the gang to be Russia-based.
Conti ransomware was part of more than 400 attacks against mostly U.S. targets between spring 2020 and spring 2021, the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) and the FBI reported in September.
Screenshot of the original message posted to Conti’s site Friday. It was later modified.
After the initial post got some attention, the message posted to the site was modified to exclude the threat against critical infrastructure. It adds that Conti does “not ally with any government and we condemn the ongoing war,” saying that the threat to use its “full capacity to deliver retaliatory measures” remains as a response to “Western warmongering and the American threats to use cyber warfare against the citizens of Russian Federation.”
In May 2021 the FBI warned that Conti was involved in at least 16 ransomware attacks targeting U.S. health care and first-responder networks in the previous year. The FBI warning came after Conti ransomware was used to attack Ireland’s Health Service Executive, which caused some medical procedures to be canceled and a COVID-19 vaccine portal to shut down — and could ultimately cost the system more than $112 million, an Irish news outlet reported this week.
“Mandiant has previously assessed that at least a portion of actors involved with CONTI ransomware are based in Russia and some criminals operating from there already have documented ties with Russian intelligence apparatus,” said Kimberly Goody, director of financial crime analysis at cybersecurity firm Mandiant. “More recently, publicly reported chat logs suggest that a key player in CONTI operations may have intended to provide support for government projects.”
Goody added that Russia’s criminal marketplace “is a resource that it may already be leaning on in this conflict.” The Russian government can either work with the groups directly, or purchase a group’s services or capability “creating simple deniable opportunities for the intelligence services.”
Former CISA Director Chris Krebs tweeted that the “question of whether the Conti ransomware gang was aligned with the [Russian government] may have answered itself.” The group’s message was “not unexpected,” wrote Krebs, now a partner at the Krebs Stamos Group consultancy.
Another analyst offered a more skeptical view of the matter.
“I wouldn’t consider this threat to be particularly serious,” Brett Callow, a threat analyst at cybersecurity firm Emsisoft, told CyberScoop. “Conti has a history of making big claims and, in this case, I suspect they lack the capability specifically to target critical infrastructure.”
That said, “the threat shouldn’t be dismissed,” he added, and urged organizations to follow CISA’s advice earlier this month to get “shields up” and prepare for potential cyberattacks.
Callow noted that a second ransomware group which calls itself the “CoomingProject” has also pledged to “help the Russian government if cyber attacks and conduct against Russia.”
CISA’s “shields up” notice said that although there’s “no specific or credible threats to the U.S. homeland at this time,” Russia’s attack on Ukraine heightens the need for cyber vigilance. A CISA spokesperson declined to comment on Conti’s threat Friday, but CISA Director Jen Easterly tweeted that “Russian retaliation against critical infrastructure could include ransomware attacks,” and reiterated the “shields up” warning.
Conti’s pledge to get involved in the Russia-Ukraine war from the outside echoes that of others — some of which may also be bluster — ranging from Russian vigilantes to the Ukrainian hacker underground to the hacktivist group Anonymous.
Updated 2/25/22: To include the updated language to Conti’s message and comments from CISA Director Jen Easterly.

This story was featured in CyberScoop Special Report: War in Ukraine





