Cloudflare reports ‘alarming surge’ in DDoS sophistication, escalation in recent months

The second quarter of 2023 has seen “an alarming escalation in the sophistication” of distributed denial-of-service attacks, Cloudflare said Tuesday, pointing to a proliferation of more targeted digital assaults designed to take down websites and other connected services.
Cloudflare, a company that mitigates DDoS attacks and provides other web services, said in its second quarter threat report that it has tracked thousands of attacks launched by a consortium of pro-Russian hacktivist groups, increases in targeted domain name system attacks, and a 600% increase in DDoS attacks on cryptocurrency websites.
Although DDoS attacks are sometimes considered unsophisticated and more of a nuisance than anything, they can be highly disruptive.
“Recovering from a DDoS attack can last much longer than the attack itself — just as a boxer might need a while to recover from a punch to the face that only lasts a fraction of a second,” Cloudfare’s Omer Yoachimik and Jorge Pacheco wrote in the report.
The Washington Post’s Tim Starks reported in June that the broader tech community is also noticing increasing intensity and craftiness of DDoS attacks, particularly concerning threats in the context of the Russian war on Ukraine and attacks on financial services providers.
Cloud-based virtual machines and virtual private servers are enabling larger attacks, the Cloudflare authors said, as part of a “new generation of botnets.” These new botnets are capable of delivering thousands of times more traffic than traditional ones. In February such an attack produced the largest DDoS attack on record, the company said at the time.
Among the concerning developments over the past three months, according to Cloudflare, is the 15% increase in HTTP DDoS attacks, which target websites and third-party gateways into those sites, even as this kind of attack was down year over year.
“It appears as though the threat actors behind these attacks have deliberately engineered the attacks to try and overcome mitigation systems by adeptly imitating browser behavior very accurately, in some cases, by introducing a high degree of randomization on various properties such as user agents and JA3 fingerprints to name a few,” the authors wrote. “In many of these attacks, it seems that the threat actors try to keep their attack rates-per-second relatively low to try and avoid detection and hide amongst the legitimate traffic.”
Microsoft suffered such an attack in early June as part of a broader assault on the company attributed to a group it calls Storm-1359, or more widely as Anonymous Sudan. The group is affiliated with a network of pro-Russian hacktivist personas and could itself be a either a direct product of or a group working in conjunction with Russian government interests, according to cybersecurity firm Truesec.
“This level of sophistication has previously been associated with state-level and state-sponsored threat actors, and it seems these capabilities are now at the disposal of cyber criminals,” the Cloudflare authors wrote.
The report notes that in June Anonymous Sudan publicly joined forces with Killnet and a persona claiming to be the resurgence of the erstwhile REvil ransomware syndicate to form the “Darknet Parliament” to target perceived enemies of the Russian government.
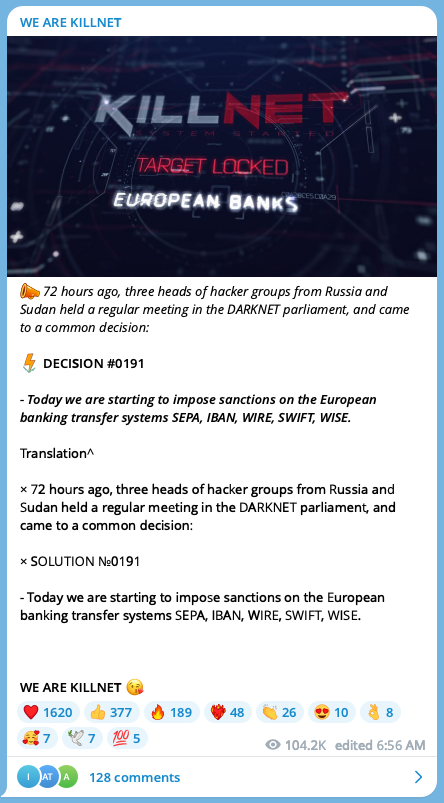
A message posted to the Killnet channel several days later said “a drunk came up with the name for the sake of trolling,” and the Cloudflare report noted that despite the trio of personas launching as many as 10,000 DDoS against Cloudflare-protected websites, the team had not “observed any novel DDoS attacks or disruptions.”
DNS laundering DDoS attacks were the most common type of DDoS over the second quarter of 2023, the report said. Laundering in this case refers to routing malicious traffic through legitimate domain name system DNS services to make the traffic appear to be legitimate.





