National Cyber Director Chris Inglis, new cyber kid on the federal block, begins to stake a claim

National Cyber Director Chris Inglis is fleshing out what, exactly, his new office plans to do with itself.
With a “strategic intent statement,” a personnel move, a pair of interviews and a newspaper op-ed, Inglis and his office on Thursday provided their most concrete objectives to date for a White House post that sprung into existence in January, and that Inglis won confirmation for in June. He joined a crowded field of feds focused on cyber, from other offices within the White House to departments and agencies like the FBI, the Department of Homeland Security’s Cybersecurity and Infrastructure Agency and the National Security Agency.
Inglis said Thursday that it’s a natural, when looking at the disparate organizations in the federal government with cybersecurity responsibilities, to wonder who’s in charge. But he said there were “more appropriate” questions.
“How do we bring coherence, how do drive public-private collaboration, how do we have some degree of performance assessment and how do we account not just for present resilience —based largely on response and mitigation — but future resilience?” he said at an event hosted by the Center for Strategic and International Studies.
The office plans to focus on both national and federal cybersecurity, assessing and reviewing budgets, supply chain security, planning and incident response, workforce development and working with Congress and the private sector.
The strategic intent document doesn’t always distinguish between when the office of the NCD will complement, rather than duplicate, the work of other agencies.
CISA, for instance, states that “it leads efforts to protect the federal ‘.gov’ domain of civilian government networks,” while the NCD strategic intent states that it “will ensure that the world-class cybersecurity we expect of critical private sector actors is reflected and propagated in the departments and agencies with which they collaborate.”
The NCD post sprung from the recommendations of the congressionally-created Cyberspace Solarium Commission. “The NCD will be the President’s principal advisor for cybersecurity-related issues, as well as lead national-level coordination of cybersecurity strategy and policy, both within government and with the private sector,” the commission’s final report stated. Commission co-chair Sen. Angus King, I-Maine, said the objective of creating an NCD was to give Congress “one throat to choke.”
But it’s been less clear sense to the Hill and others how the newest cyber job in the executive branch fits into the overarching bureaucracy. Private sector officials have said that the federal picture is murky, and sometimes daunting for breached companies, resulting in confusion about the best point-of-contact for firms dealing with a cyber incident.
At a hearing in September, Ohio Sen. Rob Portman, the top Republican on the Homeland Security and Governmental Affairs Committee, displayed a chart of cybersecurity posts within the federal government.
“Maybe it’s just me, but it seems like there’s a lot of overlapping responsibility,” he said. “The question is, who’s in charge, who’s accountable?”
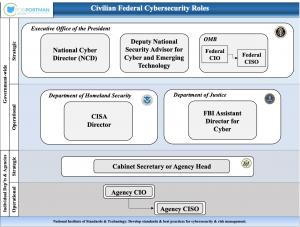
Inglis said Thursday that it was valuable to try to answer “who’s accountable for what, under what circumstances and for what purposes” rather than the “intuitive question” of “who’s in charge.”
At the September Senate hearing, Portman said he saw overlap between Inglis’ job, the Department of Homeland Security’s Cybersecurity and Infrastructure Agency and the federal chief information security officer, Chris DeRusha. Inglis on Thursday announced that DeRusha would continue to serve as CISO but take the additional responsibility of deputy national cyber director for federal cybersecurity. That move was well-received by some national security experts.
Overall, Inglis has just a handful of staffers thus far. He said he plans to have 25 by the end of the year and 75 in all.
The even bigger picture
Inglis isn’t the only one thinking of the big picture in the Biden administration. Deputy National Security Adviser for Cyber and Emerging Technology Anne Neuberger, also speaking at CSIS on Thursday, previewed the forthcoming national cybersecurity strategy.
“We put a focus on action and outcomes in the first months,” she said, meaning a national strategy took a back seat. The three focuses of that upcoming strategy will be domestic resilience, leading internationally and ensuring that the U.S. can compete in cyberspace.
Furthermore, the administration is pushing to establish more mandatory baseline cybersecurity rules for critical infrastructure.
“We did an authorities scrub on the National Security Council and we found that while there are some limited authorities … they’re largely piecemeal, and in many cases they’re not used to the degree needed in order to set a minimum required threshold to guarantee those critical services and be able to protect the nation,” she said.
The Transportation Security Administration has erected mandatory rules for pipelines, rail and air transport — to the dismay of some Republicans and industry groups. That, Neuberger said, was an example of using authorities that already exist, and she suggested more are to come.
The administration also examined sectors where their counterpart agencies lack the power to push such mandates, Neuberger said. One such area is in water cybersecurity, where the administration is seeking more authority from Congress on behalf of the Environmental Protection Agency, she said.






