As many as 165 companies ‘potentially exposed’ in Snowflake-related attacks, Mandiant says

As many as 165 organizations may be impacted by data exfiltration attacks targeting customers of the data storage firm Snowflake, Google’s Mandiant said Monday.
As details regarding the operation targeting Snowflake continue to emerge, the incident has already ensnared a slew of major companies — including Ticketmaster, Santander Group, Advance Auto Parts and others — and affected a huge number of individuals, potentially in the hundreds of millions.
Mandiant’s findings Monday point toward the widening impact of the operation against Snowflake and come as the firm works with the company to investigate this spate of breaches involving its customers. Although Snowflake itself has not been compromised, a group of hackers using credentials harvested via information stealer malware have systematically targeted Snowflake accounts that did not have multi-factor authentication enabled and Snowflake customer instances that did not have restrictions on non-trusted location access, Mandiant said. Some of the credentials used in the attacks were several years old.
Snowflake said Monday that it is “developing a plan to require” customers to implement multi-factor authentication.
The Snowflake-related attacks are being carried out by a small group of people Mandiant is tracking as UNC5537, a cluster of financially motivated attackers focused on extortion. The activity has targeted hundreds of organizations worldwide, according to Mandiant, which said that the group is perhaps made up by people in North America and at least one collaborator in Turkey.
The earliest evidence of the group’s targeting of Snowflake instances dates to April 14, and Mandiant began investigating data stolen from an unknown database five days later, the company said. By May 14, Mandiant identified multiple impacted Snowflake customer instances, and the company and Snowflake notified law enforcement May 22.
The first Snowflake customer data was offered for sale online May 24, when a user named “whitewarlock” posted what they said was Santander Group data on 30 million customers to a Russian-language cybercrime forum, according to Mandiant. The company reported May 14 that “certain information relating to customers of Santander Chile, Spain and Uruguay, as well as all current and some former Santander employees of the group had been accessed.”
Ticketmaster parent company Live Nation Entertainment said in an SEC filing that it noticed “unauthorized activity” within a third-party cloud database environment on May 20.
Meanwhile BreachForums, a key English-language cybercrime forum where stolen data is advertised and sold — including Ticketmaster’s data involving an alleged 560 million people — went offline June 9 for reasons that are not yet clear.
The site has been disrupted twice in the past two years by the FBI and a coalition of other international law enforcement agencies — most recently May 15 — only to be reconstituted days later by senior staff or other prominent users.
Telegram accounts related to BreachForums and ShinyHunters, the persona most recently in charge of BreachForums, have also been disabled or deleted.
The FBI declined to comment. Telegram did not respond to a request for comment.
Mandiant’s report Monday highlights the pervasive threat of infostealer malware, which is designed to gather credentials and other data from browsers or infected websites. Infostealer variants — including VIDAR, RISEPRO, REDLINE, RACOON STEALER, LUMMA and METASTEALER — are ubiquitous, with tens of millions of username/password combinations available for sale.
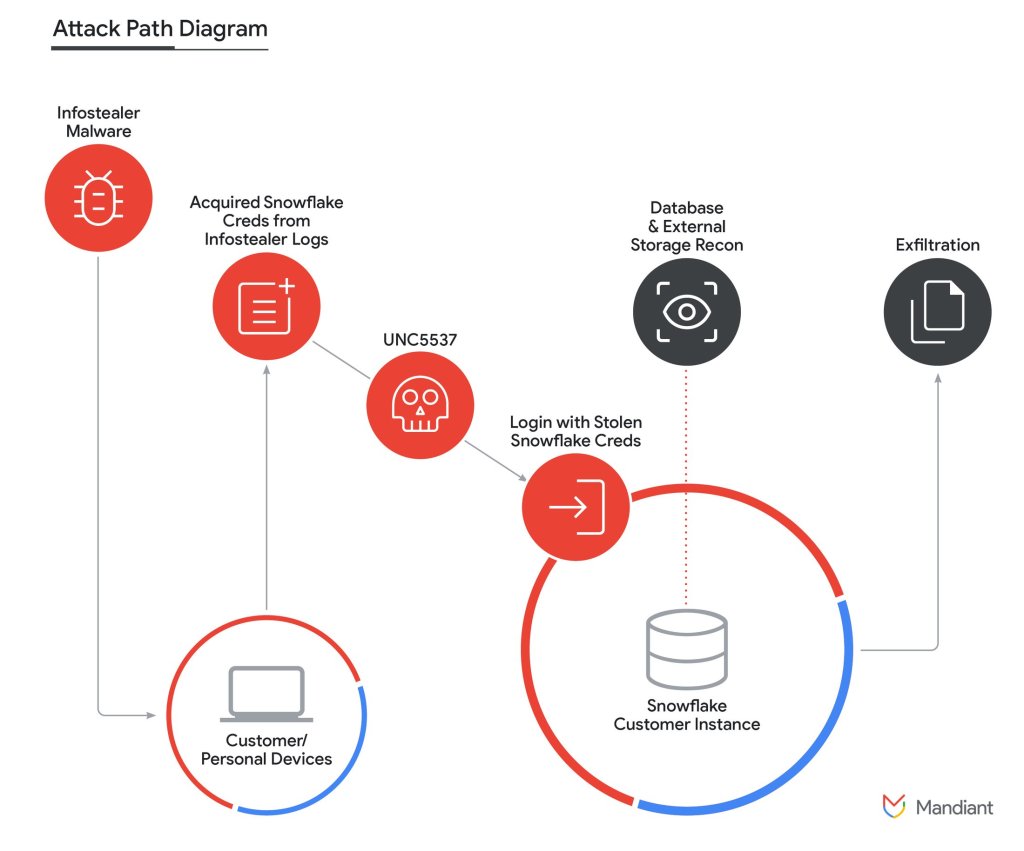
Infostealers harvest credentials, which are then packaged and sold as “logs” and used to facilitate all manner of cybercrime and other cyber-enabled activities.
The malware is sometimes included in trojanized software on corporate or personal devices, Mandiant noted. “In several Snowflake related investigations, Mandiant observed that the initial compromise of infostealer malware occurred on contractor systems that were also used for personal activities, including gaming and downloads of pirated software,” the company noted.