Google’s Triada backdoor demonstrates vulnerabilities in the mobile supply chain

Hackers in 2017 surreptitiously installed malicious software on Android phones by inserting code in apps and programs built by third-party vendors, Google said in a blog post Thursday.
The novel hacking technique was designed to load a customers’ phone with spam and unauthorized advertisements all before it even arrived in customers’ hands. When phone manufacturers wanted to include features not approved by the Android Open Source Project, like a face unlock program, Google said, those companies may hire unauthorized third-party companies to build the features for them. In this case, a malware group, known as Triada, devised a way to exploit those third parties to pre-install backdoors onto the Android devices.
“By working with the OEMs and supplying them with instructions for removing the threat from devices, we reduced the spread of preinstalled Triada variants and removed infections from the devices through the [over-the-air] updates,” Google said. “The Triada case is a good example of how Android malware authors are becoming more adept.”
Google did not specify which devices had been affected, though Ars Technica noticed 2017 research from the security vendor Dr. Web reporting that the Leagoo M5 Plues Leagoo M8, Nomu S10 and Nomu S20 had been affected.
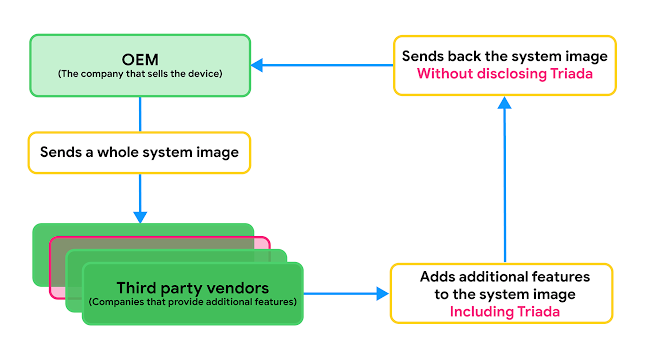
Google’s visual explanation of how Triada exploited the digital supply chain.
Word of the Triada family first surfaced in a pair of 2016 reports from Kaspersky. The malware author’s goal was to install apps capable of sending spam and “injecting tons of ads,” perhaps to commandeer affected phones to conduct advertising fraud. To make this happen, Triada proved capable of meddling with the other apps on an infected device, collecting SMS messages to capture in-app purchase information and spoofing URLs loaded in mobile browsers, among other techniques.
Google said it noticed an update to that modus operandi in 2017 when Triada evolved to become the pre-installed backdoor detailed in Thursday’s blog post.
“Triada was inconspicuously included in the system image as third-party code for additional features requested by the OEMs,” the company said. “This highlights the need for thorough ongoing security reviews of system images before the device is sold to the users as well as any time they get updated over-the-air[.]”






