NSA’s new open language for cyber-defenses will aid interoperability

Led by the NSA, a group of cybersecurity experts and vendors has been busy behind the scenes for more than a year, developing an open, standardized computer language for the command and control of cyber-defenses — OpenC2.
The idea of OpenC2 is to let different elements of cyber-defense technology communicate at machine speed — regardless of whether or not they are made by the same vendor and no matter which programming language they use.
Cyber-defenders “have to have an automated machine response,” to outpace the attacker, said NSA official Joe Brule, the original convener of the OpenC2 process. “We’re going to have to have standardized interfaces” to allow security tools from different vendors to talk to each other, he told the Gartner Security and Risk Management Summit on Tuesday.
The use of standardized interfaces and protocols enables interoperability of different tools, regardless of the vendor that developed them, the language they are written in or the function they are designed to fulfill.
Relying on human-speed response is a path to certain defeat, Brule argued. “Seventy-two percent of attacks occur in seconds to single digit minutes … defenses are statically configured and operate in isolation … changes can break an implementation,” and business processes can take weeks to cycle through.
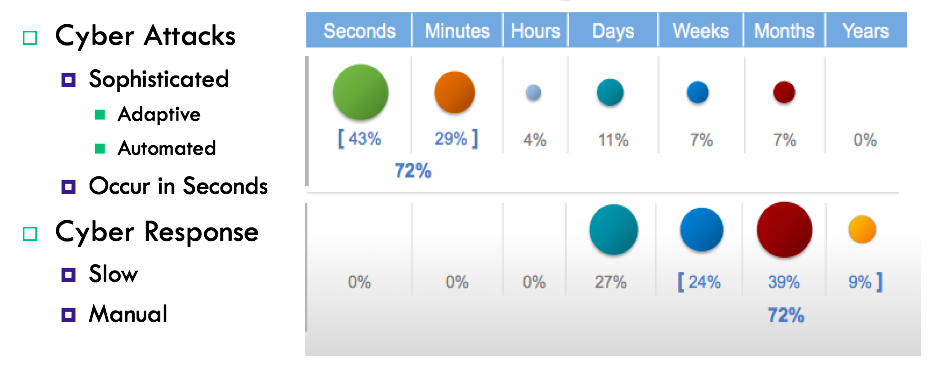
Cyber-offense and cyber-defense timelines (source: OpenC2 presentation)
OpenC2 is a limited language which simply conveys the “action” part of the cybersecurity process. It leaves aside the analytics, the “why” you are acting; the decision about “which’ action to take; and the sensing, the “what” that triggers the action in the first place.
“It’s very stripped-down,” Brule said.
“Decoupling the aspects of the command this way future-proofs the language” against technological advances, he added, because it doesn’t matter what the actuator, the technology carrying out the command, is.
Eventually, Brule predicted, the various functional blocks of different cyber-defense systems would have to be “decoupled” and equipped with standardized interfaces so that they can be integrated together in modular fashion.
“We are going to fail at cyber-defense, until we have these functional blocks, until we have standardized interfaces, we are going to fail,” he said.
Brule mocked the idea, in current circumstances, of “getting left of boom” — i.e. ahead of the problem — in cybersecurity. “Left of boom? Right now, I’d be happy to get in the same time zone” as boom, he said.
This month, Brule and the other members of the group behind OpenC2 launched their baby on the next stage of its journey, bringing it under the umbrella of the Organization for the Advancement of Structured Information Standards, or OASIS — a nonprofit international consortium that develops open IT standards.
There it joins two other cybersecurity open-standard products for automated machine-to-machine communication developed under the leadership of U.S. government agencies — STIX, a format for reporting cyberthreat intelligence; and TAXII, a protocol for sharing threat information; both developed under the wing of DHS.
“We complement each other, but we’re not dependent upon each other,” Brule said of the three products.
He said that the 88 members of the OpenC2 technical committee represented 46 companies, making it the second largest of the all the OASIS TC’s.
“This is way of the future,” he said of open standards, conceived in government-convened forums, but developed by consensus and adopted for pure utility. “We simply don’t have the [market] power to set standards” by fiat any longer, he said of the federal government.





