Smartphones can steal 3-D printing plans by listening to the printer
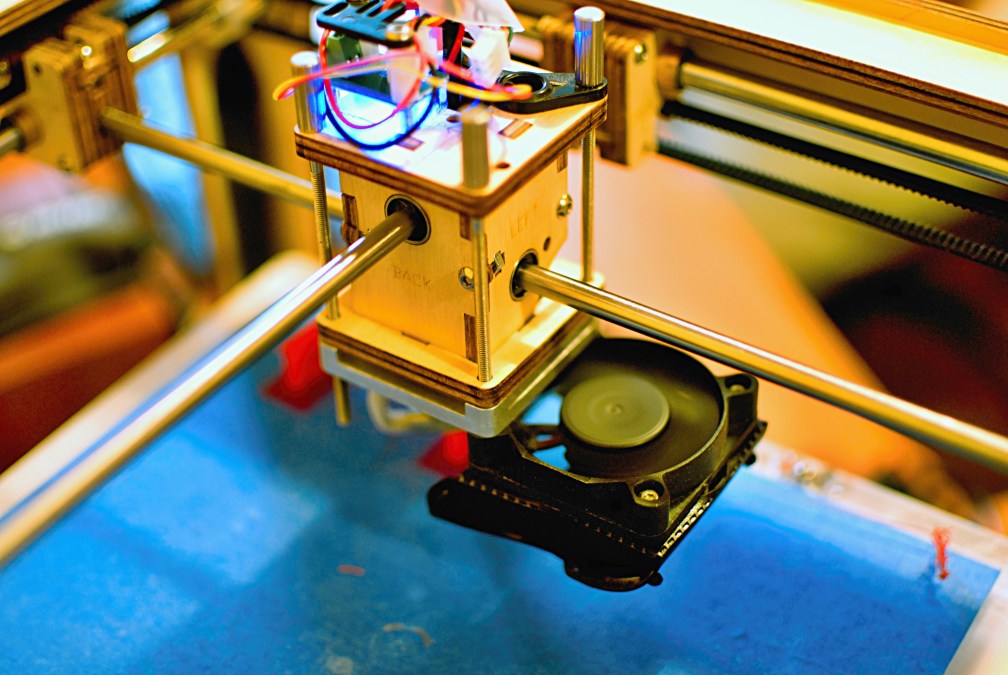
Smartphones equipped with special programming can become a sophisticated spy sensor capable of stealing designs from a 3-D printer — just by measuring the noise and electromagnetic radiation the printer emits.
Researchers from the University at Buffalo recently discovered how a smartphone on a bench about 8 inches away from a 3-D printer could allow someone to reconstruct a simple object being printed with 94 percent accuracy. Complex objects can be copied with 90 percent accuracy.
The researchers don’t give details of the application they wrote to record the acoustic and electromagnetic energy the printer is putting out, but say it uses the regular sensors of a typical smartphone.
The attack is significant, the researchers say, because 3-D printing, also known as additive manufacturing, is the next frontier in industrial production — and poised to become a multi-billion dollar business within the next few years.
This week, for instance, General Electric bought two 3-D printing companies for a total of $1.4 billion.
Moreover, although 3-D printers are often equipped with sophisticated defenses to protect them against hacking and other online threats, they are vulnerable to these so-called “side-channel” attacks in the physical realm.
“Many companies are betting on 3-D printing to revolutionize their businesses, but there are still security unknowns associated with these machines that leave intellectual property vulnerable,” said Wenyao Xu, assistant professor in the University of Buffalo’s Department of Computer Science and Engineering.
“Many IP-protected products [like cases and packaging] are prototyped with 3-D printing” and would be vulnerable to illicit reproduction by forgers or copyright thieves using this technique, Xu said.
He’s the lead author of the study, “My Smartphone Knows What You Print: Exploring Smartphone-based Side-channel Attacks Against 3-D Printers,” which will be presented at the Association for Computing Machinery’s 23rd annual Conference on Computer and Communications Security next month in Austria.
The attack basically reverse-engineers the printing blueprint by reconstructing the movement of the nozzle from the electromagnetic and acoustic energy it generates while working.
Most information came from electromagnetic waves, which accounted for about 80 percent of the useful data. The remaining 20 percent came from acoustic waves.
“The tests show that smartphones are quite capable of retrieving enough data to put sensitive information at risk,” added Buffalo’s Kui Ren, a co-author of the study.


