Emotet hackers are using Democratic Party content in email scam

A global spike in the spread of Emotet malware now includes phishing messages geared toward potential Democratic Party volunteers at hundreds of U.S. organizations, according to security researchers.
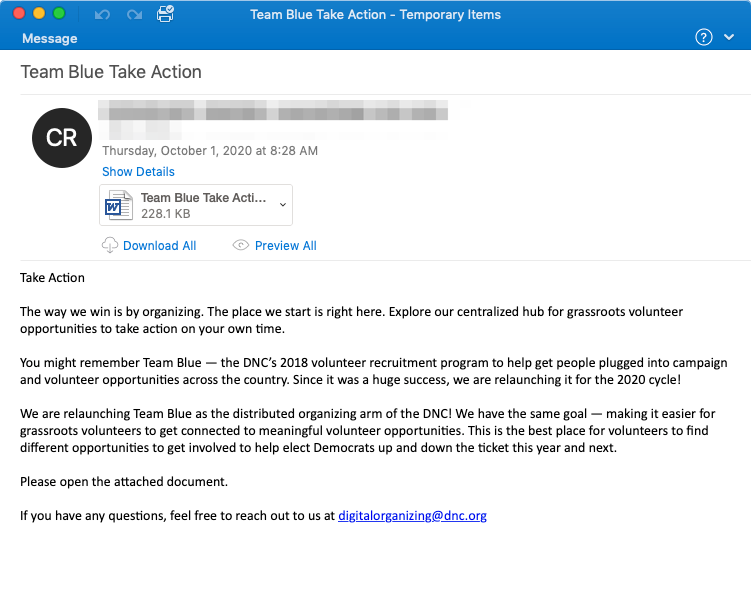
Attackers behind the Emotet hacking tool have referred to current events in their email lures before, but “historically they have not directly leveraged political themes in their messaging,” reports email security company Proofpoint. The body of this particular email is taken directly from a page on the Democratic National Committee’s website, the researchers say, and attached is a malicious Word document titled “Team Blue Take Action.”
The thousands of emails sent to U.S. targets came in the same week that interest spiked in the U.S. presidential campaign as President Donald Trump and Democratic challenger Joe Biden met in their first debate. (Trump’s announcement early Friday of a positive coronavirus test probably will not dampen Democrats’ interest in the race.)
Proofpoint stresses that despite the political content of the emails, the hackers’ goal of remains the same: Infect as many machines as possible. Emotet is a trojan that generally is used to capture people’s banking credentials. Proofpoint links the malware with a group labeled TA542, though hackers also have bought and sold the crime tool as a service, according to Barracuda Networks.
“[I]t’s unlikely that this shift is driven by any specific political ideology. Like earlier use of COVID-19 or Greta Thunberg lure themes, TA542 is attempting to reach as many intended recipients as possible by capitalizing on a popular topic,” Proofpoint says in a blog post. Scammers frequently use emotional topics, ranging from the coronavirus pandemic to major political figures, to dupe victims.
In this particular instance, the Word document contains macros that “if enabled by the intended recipient, will download and install Emotet,” Proofpoint says. Emotet then installs other malicious files. Researchers at antivirus company Malwarebytles have noted that Emotet continues to evolve as the hackers behind it update the malware to evade detection and increase its spread.
Reports of Emotet activity around the world have popped up throughout September, with cybersecurity agencies in Japan, France, Italy, the Netherlands and New Zealand warning about the malware. Microsoft’s security researchers also noted the spike.
See a sample of the phishing email described by Proofpoint below: