Hackers deploy new ransomware tool in attacks on Albanian government websites

Hackers apparently angry over the Iranian opposition group Mojahedin-e Khalq’s upcoming conference in Albania carried out disruptive cyberattacks on Albanian government sites last month, researchers from the cybersecurity firm Mandiant said Thursday.
Based on the timing of the attacks in July, technical indicators associated with the malware and the focus on MEK, the researchers are moderately confident that hackers working to further the Iranian government’s goals were behind the attack, they said.
The attacks, which forced the government of Albania to shut down online access to multiple government services, may have included a previously unknown backdoor called “ChimneySweep,” and a newly discovered ransomware tool known as “RoadSweep” to attack the government systems, the researchers said.
Additionally, the day after the initial attacks, malware known as “ZeroClear” — previously linked to to Iranian hackers — was uploaded to a public malware registry, the researchers said. It’s not clear whether that sample was used as part of the July 17 attack, but a video uploaded to a website claiming responsibility for the hacks purports to show Albanian government files being deleted.
The website, registered July 20, shares a name with a Telegram channel that became active July 25. Starting July 26, a series of news stories about the attack were posted to the channel followed by a message claiming responsibility for the attacks:
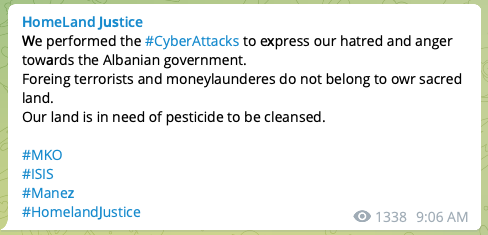
A subsequent message said the “Homeland Justice could have caused more harm and damage; but we hesitated when realizing OUR PEOPLE would also be effected.”
Both the website and the Telegram channel feature documents apparently associated with MEK members living in Albania. The hackers say they will release Albanian Prime Minster Edi Rama’s emails as well.
The prime minister tweeted July 24 that “the good news is that the aggression was successfully repelled by an Albanian-American super team, that no data was deleted, that public services are back to work!” according to a Google translation.
The MEK, which the Iranian government considers a terrorist organization, was set to hold its annual Free Iran World Summit on July 23-24 near Durres, a coastal city about a half hour west of Tirana, the Albanian capital. The U.S. Embassy in Tirana issued a security alert July 21 warning “of a potential threat” targeting the event, and urged Americans to stay away. The event was subsequently cancelled.
The RoadSweep ransomware sample referenced the coastal town in its ransom note, the researchers reported: “Why should our taxes be spent on the benefit of DURRES terrorists?”
The group’s logo — an eagle attacking a bird within a six-sided star — seems to be a direct response to the logo used by Predatory Sparrow, a sophisticated hacking group that’s pulled off a string of high-profile attacks within Iran dating back to the summer of 2021.


The researchers said they do not have evidence linking the group to a named threat group. But based on the timing, the focus on MEK and indications that the previously unknown ChimneySweep backdoor may have been used to target Farsi and Arabic speakers since 2012, the researchers are moderately confident that one or more hacking groups working in support of Iranian goals are involved.
While Iranian hackers have previously targeted dissidents and opposition groups abroad, the researchers said, this ransomware attack “is significantly more complex” than prior operations that involved ChimneySweep, raising “the possibility of a cross-team collaboration or other scenarios that we lack insight into at this time.”
The attacks occurred against the backdrop of mostly stalled multi-country talks to save the Iran nuclear deal, nearly dead since the U.S. pulled out in 2018. A new round of negotiations led by the European Unions is set to occur Thursday. The deal’s progress, or lack thereof, may be a factor in the Iranian hacking activity, the researchers said.
“The use of ransomware to conduct a politically motivated disruptive operation against the government websites and citizen services of a NATO member state in the same week an Iranian opposition groups’ conference was set to take place would be a notably brazen operation by Iran-nexus threat actors,” the Mandiant researchers wrote. “As negotiations surrounding the Iran nuclear deal continue to stall, this activity indicates Iran may feel less restraint in conducting cyber network attack operations going forward. This activity poses an active threat to public and private organizations in other NATO member states in the short term.”




